March 28, 2024
Ms. Marlene H. Dortch
Secretary
Federal Communications Commission
45 L St. NE
Washington, DC 20554
re: Regulatory Status of Wireless Messaging Service, WT Docket No. 08-7; IP-Enabled Services,
WC Docket No. 04-36
Dear Ms. Dortch:
On Tuesday, March 26, Eric Migicovsky, CEO of Beeper; Kevin Joseph, advisor to
Beeper; John Bergmayer, Legal Director of Public Knowledge; Harold Feld, Senior Vice
President of Public Knowledge; and Thomas Jones, outside counsel to Reset.tech, met with
Hannah Lepow, Legal Advisor for Media and Consumer Protection, and Shiva Goel, Legal
Advisor, Wireless, Space, & International, from Commissioner Starks office.
Beeper is a software company that develops interoperable messaging apps, including
Beeper Mini, an app that brought end-to-end encrypted iMessage communication between
iPhone and Android users. Apple blocked Beeper from providing this functionality, as
highlighted in the recent antitrust lawsuit brought by the Department of Justice, and a coalition of
states and the District of Columbia.
1
Reset.tech is a global not-for-profit dedicated to realigning
digital media markets with democratic values. Public Knowledge is a consumer rights group that
promotes freedom of expression, an open internet, and access to affordable communications
tools and creative works.
The purpose of this meeting was to inform the Commission about how Beeper Mini
works, and to discuss the legal implications of Apple’s blocking it that are relevant to the
Commission’s authority–in particular, but not limited to, interconnection requirements under
Title II of the Communications Act and possible implications with regard to the 21st Century
Communications and Video Accessibility Act.
Eric Migicovsky explained that Beeper Mini is an Android application that implements
the iMessage protocol, allowing iPhone and Android users to send and receive encrypted
messages with each other. At present, Apple bundles all its text messaging capability into its
Messages App. When Apple users communicate with other Apple users, they have access to
1
Complaint, United States v. Apple Inc., No. 2:24-cv-04055 (D.N.J. filed Mar. 21, 2024),
https://www.justice.gov/opa/media/1344546/dl?inline.

features such as end-to-end encryption, high-resolution images, delivery receipts, the ability to
seamlessly participate in group texts, and more. These texts appear in a “blue bubble” which
highlights these improved functionalities. But when Apple users attempt to text Android users
(or when Android users text Apple users), Apple restricts these texts to SMS — which lacks
these enhanced features. To highlight the limitations of SMS as compared to Apple’s Message
app, texts between Apple users and Android users are displayed in a green bubble. A technical
explanation of how Beeper functions is attached to this filing, as well as relevant passages from
the DOJ’s complaint.
Public Knowledge reiterated its support for Title II classification of interconnected
VOIP,
2
and of SMS text messaging (SMS). These services are “telecommunications” in that they
provide “the transmission, between or among points specified by the user, of information of the
user’s choosing, without change in the form or content of the information as sent and received.”
3
Public Knowledge, joined by other public interest groups, first petitioned the FCC to
classify SMS as “telecommunications” in 2007,
4
after Verizon blocked access to SMS short
codes to NARAL (now known as Reproductive Freedom for All). The Commission put this
petition out for public comment in January 2008,
5
but took no subsequent action. In 2015,
Twilio filed a petition for an expedited declaratory ruling, asking the Commission “to declare
that messaging services are governed by Title II” of the Communications Act. The Commission
put this petition out for public comment as well,
6
and again took no immediate action.
In December 2018, under new leadership, the Commission issued a Declaratory Ruling
that SMS was a Title I information service.
7
Public Knowledge, joined by other public interest
groups, filed a petition for reconsideration, arguing among other things that the Declaratory
Ruling’s reasoning was flawed.
8
The DC Circuit subsequently validated this position by
8
Petition for Reconsideration of Public Knowledge et al., WT Docket No. 08-7, (filed Jan. 28, 2019),
https://publicknowledge.org/wp-content/uploads/2021/11/PK_et_al_SMS_Order_recon.pdf. See also Reply to
Oppositions of Public Knowledge, WT Docket No. 08-7 (April 2, 2019),
https://publicknowledge.org/policy/fcc-sms-ruling-reply-to-opposition.
7
Petitions for Declaratory Ruling on Regulatory Status of Wireless Messaging Serv., Declaratory Ruling, WT
Docket No. 08-7, 33 FCC Rcd 12075 (2018), https://docs.fcc.gov/public/attachments/FCC-18-178A1.pdf.
6
WTB Seeks Comment on a Petition for Declaratory Ruling Clarifying the Regulatory Status of Mobile Messaging
Services, WT Docket No. 08-7, 80 FR 69630 (2015), https://docs.fcc.gov/public/attachments/DA-15-1169A1.pdf.
5
Comment Sought on Petition for Declaratory Ruling That Text Messages and Short Codes Are Title II Services or
Are Title I Services Subject to Section 202 Non-Discrimination Rules, WT Docket No 08-7, 73 FR 4866 (2008),
https://docs.fcc.gov/public/attachments/DA-08-282A1.pdf
4
Petition of Public Knowledge et al. for Declaratory Ruling that Text Messaging and Short Codes are Title II
Services or are Title I Services Subject to Section 202 Nondiscrimination Rules, WT Docket No. 08-7, (filed Dec.
11, 2007), https://publicknowledge.org/policy/fcc-petition-for-text-messaging-and-short-codes.
3
47 U.S.C. § 153(50).
2
Petition of Public Knowledge et al. for Declaratory Ruling That Facilities-Based Interconnected VoIP & Nomadic
Interconnected VoIP Are Title II Services, RM-____ (filed Mar. 2, 2022),
https://publicknowledge.org/wp-content/uploads/2022/03/VOIP-Declaratory-Ruling-Petition_03-02-22.pdf.
2

rejecting the same reasoning in the broadband context in Mozilla .
9
The Commission put this
petition for reconsideration out for public comment in March 2019,
10
but took no subsequent
action.
During this time, SMS has become more important than ever. Smartphones have
achieved almost universal adoption. Schools and governments use SMS to communicate with
parents and the public. One-time security codes for accessing banking services are sent via
SMS, and SMS, as a carrier-based service, remains the only way senders can be sure to reach
nearly every member of the public, relative to non-carrier services like WhatsApp that require
users to install and set up a third-party app. The problems caused by the Commission’s inaction,
and flawed actions on this subject, have not gone away. If anything they have gotten worse, and
though the FCC and FTC have taken actions directed at the scourge of robotexts and scams,
11
stronger legal authority would allow the Commission to take swifter and firmer action.
Non-carrier services like iMessage may also fit the definition of “telecommunications.”
Apple, via the built-in and uninstallable Messages app on the iPhone, combines SMS and
iMessage into one seamless user experience—which users experience as “green bubbles” (SMS)
and “blue bubbles” (iMessage).
12
Like with interconnected VOIP services, though with text and
media messages instead of calls, Apple allows users to receive communications “that originate
on the public switched telephone network” and to send messages that “terminate... [on] the
public switched telephone network.”
13
As the DOJ notes in its recent lawsuit against Apple,
Apple has prevented third-party apps like WhatsApp and Beeper from integrating with SMS as it
does with its bundled app. Further, it has been slow to adopt industry standards like RCS that
would improve cross-platform messaging, and has taken affirmative steps to block Beeper’s
attempt to interoperate with iMessage.
13
47 CFR § 9.3.
12
In the Pulver.com Petition, the Commission distinguished between services that did not provide transport and
relied on a database of user names which the service provider independently stores, and services which provided
transport and/or relied on North American Numbering Plan (NANP) phone numbers. In the 20 years since then, the
Commission has not considered how technological and market changes may have changed the underlying reasoning
in Pulver.com . But the Commission need not go so far as to reconsider Pulver to reach the conclusion that iMessage
and SMS are properly classified as Title II.
11
E.g., Targeting and Eliminating Unlawful Text Messages, CG Docket No. 21-402, Report and Order and Notice of
Proposed Rulemaking, 38 FCC Rcd 2744 (2023); FTC, IYKYK: The Top Text Scams of 2022,
https://www.ftc.gov/news-events/data-visualizations/data-spotlight/2023/06/iykyk-top-text-scams-2022.
10
Petition for Reconsideration of a Declaratory Ruling on Regulatory Status of Wireless Messaging Service, 84 FR
8497 (2019).
9
Mozilla Corp. v. FCC , 940 F.3d 1 (D.C. Cir. 2019).
3

Beeper also highlighted a recent letter from the American Economic Liberties Project et
al.,
14
consistent with arguments put forward by Commissioner Carr,
15
that Apple’s blocking of
Beeper Mini may violate the 21st Century Communications and Video Accessibility Act.
16
The
letter argues that Apple’s actions to block Beeper Mini’s functionality with iMessage may have
violated the FCC’s Part 14 rules, which are based on the CVAA. These rules require “covered
providers,” including Apple, to ensure accessibility and usability of advanced communications
services and equipment for people with disabilities. By impeding Beeper Mini’s interoperability
with iMessage, and given the accessibility shortcomings of SMS relative to iMessage, Apple has
potentially violated the rule stating that covered providers “shall not install network features,
functions, or capabilities that impede accessibility and usability.”
17
Interoperability and interconnection are core Title II requirements with a long pedigree.
In Carterfone , the Commission required AT&T to allow third-party equipment to be used with
the telephone system,
18
and followed this up with standard-setting activity designed to facilitate
interconnection and industry standardization.
19
The Commission has used its Title II authority to
promote competition and protect consumers in a variety of contexts, such as requiring
interoperability measures like number portability. The Commission has also used its Title II
authority to promote accessibility, through the establishment of TTY rules and other measures.
The Title II toolbox is available to be used for pro-competition, public interest obligations, and is
relevant to the current situation with SMS and iMessage. Just as the Commission used its Title II
authority to promote competition and protect consumers in the telephone context, it can use that
same authority to promote competition and protect consumers in the context of SMS and
iMessage. By classifying these services as Title II telecommunications services, the Commission
could ensure that they are subject to the same pro-competition, pro-consumer rules that have
long applied to other important telecommunications services.
Respectfully submitted,
/s/ John Bergmayer
Legal Director
Public Knowledge
cc: Hannah Lepow, Shiva Goel
19
The FCC’s rules regarding interconnection between telephone networks and “terminal equipment,” which
reference standards such as the RJ11 phone jack, are codified in its Part 68 rules. See 47 C.F.R. § 68.1-68.614; FCC,
https://www.fcc.gov/part-68.
18
Use of the Carterfone Device in Message Toll Telephone Service, 13 FCC 2d 420 (1968).
17
47 CFR § 14.20.
16
Pub. Law No. 111-260, codified at 47 U.S. Code § 617 et seq.
15
Emma Roth, FCC Commissioner Wants to Investigate Apple over Beeper Mini Shutdown , The Verge (Feb. 12,
2024), https://www.theverge.com/2024/2/12/24071226/fcc-commissioner-brendan-carr-apple-beeper-mini.
14
Letter from the American Economic Liberties Project et al. to The Honorable Jessica Rosenworcel, Chairwoman,
FCC (Feb. 27, 2024),
https://www.economicliberties.us/wp-content/uploads/2024/02/2024-02-27-FCC-Apple-Beeper-Mini-Letter.pdf.
4
How Beeper Mini Works
It's a technical deep dive, so buckle up!
BEEPER
DEC 05, 2023
42 Share
!"#$"%&'())"*%)+(,%-./0%1/,)%)/%+".1%2/3%3*4"',)5*4%+/&%6""1"'%7(*(%&/'8,9%:)%6""1"';%&"
-".("$"%)+5)%()%(,%<'()(<5.%=/'%2/3%)/%-"%5-."%)/%)'3,)%)+"%,/>&5'"%)+5)%2/3%3,";%",1"<(5..2
,/?")+(*0%5,%(?1/')5*)%5*4%,"*,()($"%5,%2/3'%<+5)%5119%!"%&/'8%)/%"5'*%5*4%8""1%2/3'
)'3,)%(*%)+'""%&52,@
A9% B'5*,15'"*<2%C%,(*<"%&"%,)5')"4%6""1"'%D%2"5',%50/;%&"#$"%-""*%)58(*0%/11/')3*()(",
.(8"%)+(,%)/%"E1.5(*%+/&%6""1"'%&/'8,9%!"%+5$"%5%1'/34%+(,)/'2%/=%-3(.4(*0%1'/43<),;
.(8"%F"--.";%5*4%,)5*4%13-.(<.2%-"+(*4%/3'%&/'89
G9% H1"*%,/3'<"%C%"5<+%?5I/'%1("<"%/=%,/>&5'"%)+5)%&"#$"%-3(.)%)/%(*)"'5<)%&()+%/)+"'%<+5)
Turn
your
phone
number
blue
New
Message
To:
+1
(415)
555-5555

*")&/'8,%(,%/1"*%,/3'<"%5)%0()+3-9</?J-""1"'9
D9% F'($5<2%5*4%,"<3'()2C5.(0*"4%-3,(*",,%?/4".%C%&"%?58"%0'"5)%,/>&5'"%5*4%<+5'0"%5
,?5..%,3-,<'(1)(/*%=""9%K(?1."%5,%)+5)9%L/%54,9%M/3'%45)5%,)52,%1'($5)"9
N"54%)+"%"*)('"%1/,)%=/'%)+"%=3..%,)/'29%BOPN@%)+"%=/../&(*0%="5)3'",%/=%6""1"'%7(*(%"*,3'"
)+5)%5..%</??3*(<5)(/*%(,%"*<'21)"4%5*4%,"<3'"9
:..%?",,50",%5'"%"*4C)/C"*4%"*<'21)"4%-"=/'"%-"(*0%,"*)9%6""1"'%Q5*4%:11."R%<5**/)
,""%2/3'%?",,50",9
S*<'21)(/*%8"2,%*"$"'%."5$"%2/3'%4"$(<"9
6""1"'%7(*(%</**"<),%4('"<).2%)/%:11."%,"'$"',9%B+"'"%(,%*/%75<%,"'$"'%'".52;%.(8"
/)+"'%511,9
L/%:11."%TP%(,%'"U3('"49%6""1"'%4/",%*/)%+5$"%5<<",,%)/%2/3'%:11."%5<</3*)9
M/3'%</*)5<)%.(,)%*"$"'%."5$",%2/3'%4"$(<"9
P/*#)%-".("$"%)+(,%(,%1/,,(-."V%B'2%)+"%/1"*C,/3'<"%F2)+/*%1'//=%/=%</*<"1)%/*%2/3'%/&*
</?13)"'%)/%,""%=/'%2/3',".=9%K"<3'()2%'","5'<+"',%5'"%(*$()"4%)/%$"'(=2%5..%<.5(?,%)+5)%&"
?58";%,""%511"*4(E%-"./&9
6""1"'%7(*(%&/'8,%4(W"'"*).2%)+5*%6""1"'%X./34%(*%(?1/')5*)%&52,%)+5)%(*<'"5,"%2/3'
1'($5<2%5*4%,"<3'()29%6""1"'%7(*(%(,%5%,)5*45./*"%:*4'/(4%5119%T)%4/",%*/)%'"U3('"%5%<./34
,"'$"'%)/%,"*4%5*4%'"<"($"%?",,50",9%T)%5.,/%(?1."?"*),%:11."#,%"*4C)/C"*4%"*<'21)(/*
1'/)/</.%*5)($".2%&()+(*%)+"%:*4'/(4%511%(),".=9%:..%?",,50",%5'"%"*4C)/C"*4%"*<'21)"4
-"=/'"%)+"2%5'"%)'5*,?())"4%4('"<).2%='/?%2/3'%4"$(<"%)/%:11."%,"'$"',9%O"5'*%?/'"%5-/3)
(7",,50"%"*<'21)(/*%/*%:11."%F.5)=/'?%K"<3'()2%150"9
B+(,%(,%*/&%1/,,(-."%-"<53,"%)+"%(7",,50"%1'/)/</.%5*4%"*<'21)(/*%+5$"%-""*%'"$"',"
"*0(*""'"4%-2%II)"<+;%5%,"<3'()2%'","5'<+"'9%O"$"'50(*0%)+(,%'","5'<+;%6""1"'%7(*(
(?1."?"*),%)+"%(7",,50"%1'/)/</.%./<5..2%&()+(*%)+"%5119%:..%?",,50",%5'"%,"*)%5*4
Security and privacy
How it works

'"<"($"4%-2%6""1"'%7(*(%:*4'/(4%511%4('"<).2%)/%:11."#,%,"'$"',9%B+"%"*<'21)(/*%8"2,
*""4"4%)/%"*<'21)%)+","%?",,50",%*"$"'%."5$"%2/3'%1+/*"9%L"()+"'%6""1"';%:11.";%*/'
5*2/*"%"E<"1)%)+"%(*)"*4"4%'"<(1("*),%<5*%'"54%2/3'%?",,50",%/'%5))5<+?"*),9%6""1"'%4/",
*/)%+5$"%5<<",,%)/%2/3'%:11."%<'"4"*)(5.,9
!"%-3(.)%6""1"'%7(*(%-2%5*5.2Y(*0%)+"%)'5Z<%,"*)%-")&""*%)+"%*5)($"%(7",,50"%511%5*4
:11."#,%,"'$"',;%5*4%'"-3(.4(*0%/3'%/&*%511%)+5)%,"*4,%)+"%,5?"%'"U3",),%5*4%3*4"',)5*4,
)+"%,5?"%'",1/*,",9%O"5'*%?/'"%-2%'"54(*0%II)"<+#,%-./0%1/,);%(7",,50"%SE1.5(*"4;%5*4%+(,
1'//=C/=C</*<"1)%F2)+/*%(?1."?"*)5)(/*%/*%[()+3-9%:*2/*"%<5*%4/&*./54%)+(,%</4";%'3*
()%/*%5*2%</?13)"'%)+5)%,311/'),%F2)+/*;%./0(*%)/%)+"('%(7",,50"%5<</3*);%5*4%,"*4%5*4
'"<"($"%(7",,50"%1'/)/</.%?",,50",9%L/%:11."%+5'4&5'"%'"U3('"49
:*/)+"'%<+5*0"%(,%)+5)%6""1"'%7(*(%4/",%*/)%3,"%)+"%75)'(E%1'/)/</.;%"*<'21)(/*%/'%</4"
.(8"%6""1"'%X./349%T)%(,%5%</?1.")".2%*"&%</4"-5,";%$"',3,%/3'%\',)%:*4'/(4%511;%&+(<+%&5,
5%=/'8%/=%S."?"*)9%T*%)+"%=3)3'";%&"%5'"%1.5**(*0%)/%544%75)'(E%*")&/'8%,311/')%-5<8%(*;
5./*0%&()+%,311/')%=/'%)+"%A]%/)+"'%<+5)%*")&/'8,%(*%6""1"'%X./349%N"54%?/'"%5-/3)%/3'
'/54?519
!+"*%2/3%\',)%,)5')%)+"%6""1"'%7(*(%511%5*4%,(0*%(*%&()+%[//0.";%5%'"0(,)'5)(/*%'"U3",)%(,
,"*)%)/%/3'%6""1"'%:FT%K"'$"'9%B+(,%,"'$(<"%/*.2%"E(,),%)/%$"'(=2%2/3'%,3-,<'(1)(/*%,)5)3,;%5,
&"..%5,%0($"%/3'%,311/')%)"5?%)+"%(*=/'?5)(/*%)+"2%*""4%)/%4"-30%5*2%(,,3",%)+5)%2/3%?52
-"%'3**(*0%(*)/%Q(*<.34(*0%2/3'%*5?"%5*4%"?5(.%544'",,R9%L/%(7",,50"%<'"4"*)(5.,%/'
?",,50",%5'"%)'5*,?())"4%)+'/30+%)+","%,"'$"',;%&+(<+%5'"%=/'%6""1"'%7(*(%5<</3*)
?5*50"?"*)%/*.29
:>"'%)+5);%2/3%5'"%1'/?1)"4%)/%5../&%*/)(\<5)(/*,;%&+(<+%,"*4,%5%13,+%)/8"*%)/%6""1"'
F3,+%L/)(\<5)(/*%,"'$(<";%&+(<+%"*5-.",%/3'%,"'$"',%)/%,"*4%13,+%*/)(\<5)(/*,%)/%2/3'
:*4'/(4%4"$(<"9%B+","%13,+%*/)(\<5)(/*,%4/%*/)%</*)5(*%)+"%</*)"*),%/=%?",,50",9
Inside the Beeper Mini Android app
1. Sign in
2. Permissions and registration

L"E);%2/3%5'"%1'/?1)"4%)/%0'5*)%</*)5<)%.(,)%5*4%K7K%1"'?(,,(/*%5<<",,9
X/*)5<)%.(,)%5<<",,%(,%3,"4%)/%?5)<+%1+/*"%*3?-"',%)/%</*)5<)%*5?",;%5*4%4(,1.52
1'/\."%1(<)3'",9%M/3'%</*)5<)%.(,)%(,%*"$"'%,"*)%)/%6""1"'%,"'$"',9
K7K%5<<",,%(,%3,"4%)/%,"*4%5*%K7K%)"E)%?",,50"%='/?%2/3'%*3?-"'%)/%:11."#,
^[5)"&52_%,"'$(<"9%B+"%05)"&52%,"*4,%5%'",1/*,"%$(5%K7K;%5*4%)+"%</*)"*),%='/?%)+5)
K7K%'",1/*,"%5'"%,"*)%)/%:11."%)/%'"0(,)"'%2/3'%1+/*"%*3?-"'%5,%5%-.3"%-3--."9%M/3'
K7K%<+5)%+(,)/'2%(,%5.,/%3,"4%)/%4")"'?(*"%(=%5*2%/=%2/3'%'"<"*)%K7K%<+5),%&"'"%&()+
1"/1."%&+/%+5$"%(F+/*",9%T=%,/;%)+","%<+5),%5'"%,+/&*%(*%)+"%(*-/E9
T)#,%5)%)+(,%1/(*)%)+5)%)+"%511%0"*"'5)",%"*<'21)(/*%8"2,%)+5)%5'"%3,"4%=/'%"*4C)/C"*4
"*<'21)"4%?",,50(*09%B+"%13-.(<%8"2%(,%,"*)%)/%:11."%,"'$"',;%5*4%)+"%1'($5)"%8"2,%5'"
,)/'"4%(*%)+"%:*4'/(4%4"$(<"%./<5.%\.",2,)"?9%6""1"'%7(*(%(,%*/&%,(0*"4%(*9
H1)(/*5..2;%2/3%?52%5.,/%,(0*%(*%)/%2/3'%:11."%TP%)/%"*5-."%,"*4(*0J'"<"($(*0%='/?%2/3'
"?5(.%544'",,9%B+(,%&(..%5.,/%"*5-."%2/3%)/%,"*4%5*4%'"<"($"%?",,50",%='/?%/)+"'%:11."
4"$(<",%.(8"%(F54%/'%75<,9%B+"%:11."%TP%./0(*%,"*4,%2/3'%3,"'*5?";%15,,&/'4%5*4%5%GC
=5<)/'%</4"%3,(*0%"*<'21)"4%`BBFK%'"U3",),%4('"<).2%)/%:11."%,"'$"',9
3. Optional Apple ID sign in
4. Sending and receiving messages

:11."#,%(7",,50"%1'/)/</.%&/'8,%/$"'%:11."%F3,+%L/)(\<5)(/*%,"'$(<";%&+(<+%?/,)
4"$"./1"',%&/3.4%-"%=5?(.(5'%5,%)+"%,"'$(<"%)+5)%5../&,%)+"?%)/%,"*4%13,+%*/)(\<5)(/*,%)/
)+"('%(HK%511.(<5)(/*,9%a/'%(7",,50"%1'/)/</.;%5..%?",,50(*0%)'5Z<%b/&,%/$"'%)+(,%,"'$(<"
(*%-/)+%4('"<)(/*,;%"*<'21)"4%&()+%8"2,%0"*"'5)"4%./<5..2%/*%"5<+%4"$(<"9%6""1"'%7(*(
</**"<),%)/%:FL,%/$"'%BXF;%3,(*0%)+"%<'"4"*)(5.,%0"*"'5)"4%43'(*0%)+"%./0(*%1'/<",,9
:%1"',(,)"*)%</**"<)(/*%)/%:FL,%(,%*""4"4%)/%-"%*/)(\"4%/=%*"&%(*</?(*0%?",,50",%(*
'"5.C)(?"9%H*%5*%(F+/*";%5*%:FL,%</**"<)(/*%(,%?5(*)5(*"4%-2%)+"%/1"'5)(*0%,2,)"?;%5*4
</**"<)"4%5)%5..%)(?",9%T*%6""1"'%7(*(;%)+"%</**"<)(/*%<5*%/*.2%-"%?5(*)5(*"4%&+"*%)+"
511%(,%'3**(*0;%,(*<"%:*4'/(4%4/",%*/)%,311/')%:FL,%*5)($".29
B/%&/'8%5'/3*4%)+(,%.(?()5)(/*;%&"%-3(.)%6""1"'%F3,+%L/)(\<5)(/*%,"'$(<"%Q6FL,R9%6FL,
</**"<),%)/%:11."#,%,"'$"',%/*%2/3'%-"+5.=%&+"*%6""1"'%7(*(%:*4'/(4%511%(,*#)%'3**(*09
!"%<5*%4/%)+(,%&+(."%1'","'$(*0%3,"'%1'($5<2%)+5*8,%)/%:11."%,"15'5)(*0%)+"%<'"4"*)(5.,

*""4"4%)/%</**"<)%)/%:FL,%)/%,"*4%5*4%'"<"($"%</*)"*)%Q)+"%^13,+_%<'"4"*)(5.,R%5*4%)+"
8"2,%*""4"4%)/%"*<'21)%5*4%4"<'21)%?",,50",%Q)+"%^(4"*)()2_%8"2,R9%F3,+%<'"4"*)(5.,%<5*%-"
,+5'"4%,"<3'".2%&()+%)+"%6""1"'%F3,+%L/)(\<5)(/*%,"'$(<";%5*4%6FL,%<5*%</**"<)%)/%:FL,
/*%2/3'%-"+5.=9%!+"*"$"'%6FL,%'"<"($",%5*%"*<'21)"4%?",,50"%)+5)%()%&/*#)%-"%5-."%)/
4"<'21);%()%,(?1.2%4(,</**"<),%='/?%:FL,%5*4%,"*4,%5*%aX7%13,+%*/)(\<5)(/*%)/%&58"%31
)+"%:*4'/(4%511;%&+(<+%)+"*%</**"<),%)/%:FL,;%4/&*./54,;%4"<'21),%5*4%1'/<",,",%)+"
(*</?(*0%?",,50"9%6FL,%<5*%/*.2%)"..%&+"*%5%*"&%?",,50"%(,%&5()(*0%=/'%2/3%C%()%4/",%*/)
+5$"%<'"4"*)(5.,%)/%,""%/'%4/%5*2)+(*0%".,"9
6FL,%&(..%-"%*/)(\"4%&+"*%2/3%'"<"($"%5%?",,50";%-3)%&()+/3)%)+"%"*<'21)(/*%8"2,%()%<5*#)
4"<'21)%5*2)+(*0%6FL,%'"<"($",9%:.,/;%&()+/3)%)+"%(4"*)()2%<'"4"*)(5.,;%6FL,%<5*#)%,"*4
?",,50",%/*%2/3'%-"+5.=9%T=%2/3%4/*#)%?(*4%*/)%'"<"($(*0%'"5.C)(?"%13,+%*/)(\<5)(/*,%=/'
*"&%?",,50",;%2/3'%6FL,%<5*%-"%4(,5-."4%"*)('".2%-2%0/(*0%)/%K"))(*0,%→%75*50"
X/**"<)(/*%→%S*5-."%F3,+9
!+"*%2/3%<'"5)"%5%*"&%<+5);%)+"%1+/*"%*3?-"'%/'%"?5(.%544'",,%/=%2/3'%(*)"*4"4%'"<(1("*)
(,%)'5*,?())"4%)/%:11."%,"'$"',9%T=%)+"%</*)5<)%(,%/*%(7",,50";%5%13-.(<%8"2%(,%'")3'*"49
K"*4(*0%?",,50",%(,%"$"*%,(?1."'9%!+"*%2/3%+()%,"*4;%)+"%?",,50"%(,%"*<'21)"4%&()+%)+"
13-.(<%8"2,%/=%)+"%(*)"*4"4%'"<(1("*),%5*4%,"*)%4('"<).2%)/%:11."%,"'$"',%$(5%5*%KKO
"*<'21)"4%BXF%</**"<)(/*%/$"'%:FL,9
6""1"'%7(*(%</**"<),%)/%5%="&%/)+"'%,"'$(<",%5,%15')%/=%(),%/1"'5)(/*9%!"%3,"%5%,".=C+/,)"4
(*,)5..5)(/*%/=%N344"',)5<8%Q+))1,@JJ'344"',)5<89-""1"'C)//.,9</?R%=/'%5*5.2)(<,%5*4
4(50*/,)(<%"$"*),;%&+(<+%&"%3,"%=/'%(?1'/$(*0%)+"%511%-3)%<5*%-"%4(,5-."4%(*%K"))(*0,%→
F'"="'"*<",%→K+5'"%P(50*/,)(<,9%!"%3,"%H*"K(0*5.%)/%,"*4%"43<5)(/*%5*4%5<</3*)%'".5)"4
13,+%*/)(\<5)(/*,;%5*4%N"$"*3"X5)%)/%+".1%(*)"0'5)"%[//0."%F.52%,3-,<'(1)(/*,9
H)+"'%)+5*%)+5);%)+5)#,%()c%L/%/)+"'%,"'$"',%/'%,"'$(<",%5'"%3,"49%6""1"'%7(*(%8""1,%2/3'
?",,50(*0%,"<3'"%-2%8""1(*0%5..%?",,50(*0%<'"4"*)(5.,;%8"2,;%?",,50",%5*4%?"4(5%./<5.%)/
2/3'%1+/*";%5*4%/*.2%,"*4,%)+"?%4('"<).2%)/%:11."#,%,"'$"',%5>"'%"*<'21)(*0%)+"?%&()+
(7",,50"#,%"*4C)/C"*4%"*<'21)(/*%5.0/'()+?9
5. Analytics and other services
!"%$5.3";%5<)35..2;%&"%)'"5,3'"%=""4-5<89%T=%2/3%'3*%(*)/%5%-30%/'%+5$"%5%="5)3'"%'"U3",);
)+"'"#,%5%-3))/*%(*C511%)/%'"1/')%5%1'/-."?9%!"%'"54%"$"'2%,(*0."%'"1/')9
Brad Murray and Eric Migicovsky
6""1"'%</=/3*4"',
B/%&'()"%)+(,%-./0%1/,);%&"%1"'=/'?"4%5%'"4%)"5?%5*5.2,(,%/*%/3'%/&*%5119%!"%?54"
"E)"*,($"%3,"%/=%)+"%"E<".."*)%?()?1'/E2%1'/I"<)%)/%<51)3'"%)+"%*")&/'8%)'5Z<%</?(*0
='/?%5%'"5.%1+/*"%'3**(*0%5%?/4(\"4%$"',(/*%/=%)+"%6""1"'%7(*(%<.("*)9%:%?/4(\"4%$"',(/*
&5,%*""4"4%=/'%)+(,%5*5.2,(,%(*%/'4"'%)/%4(,5-."%<"')(\<5)"%1(**(*0;%,/%)+5)%)+"%6""1"'%7(*(
:*4'/(4%511%&/3.4%5<<"1)%-"(*0%</**"<)"4%)/%?()?1'/E2%(*,)"54%/=%/*.2%5<<"1)(*0%:11."#,
<"')(\<5)",%=/'%)+5)%</**"<)(/*9%T=%'","5'<+"',%&/3.4%.(8"%5%</12%/=%)+(,%$"',(/*%/=%6""1"'
7(*(%Q&()+%<"')%1(**(*0%4(,5-."4R%)/%1"'=/'?%5%,(?(.5'%5*5.2,(,;%1."5,"%</*)5<)%3,%5)
,"<3'()2d-""1"'9</?9
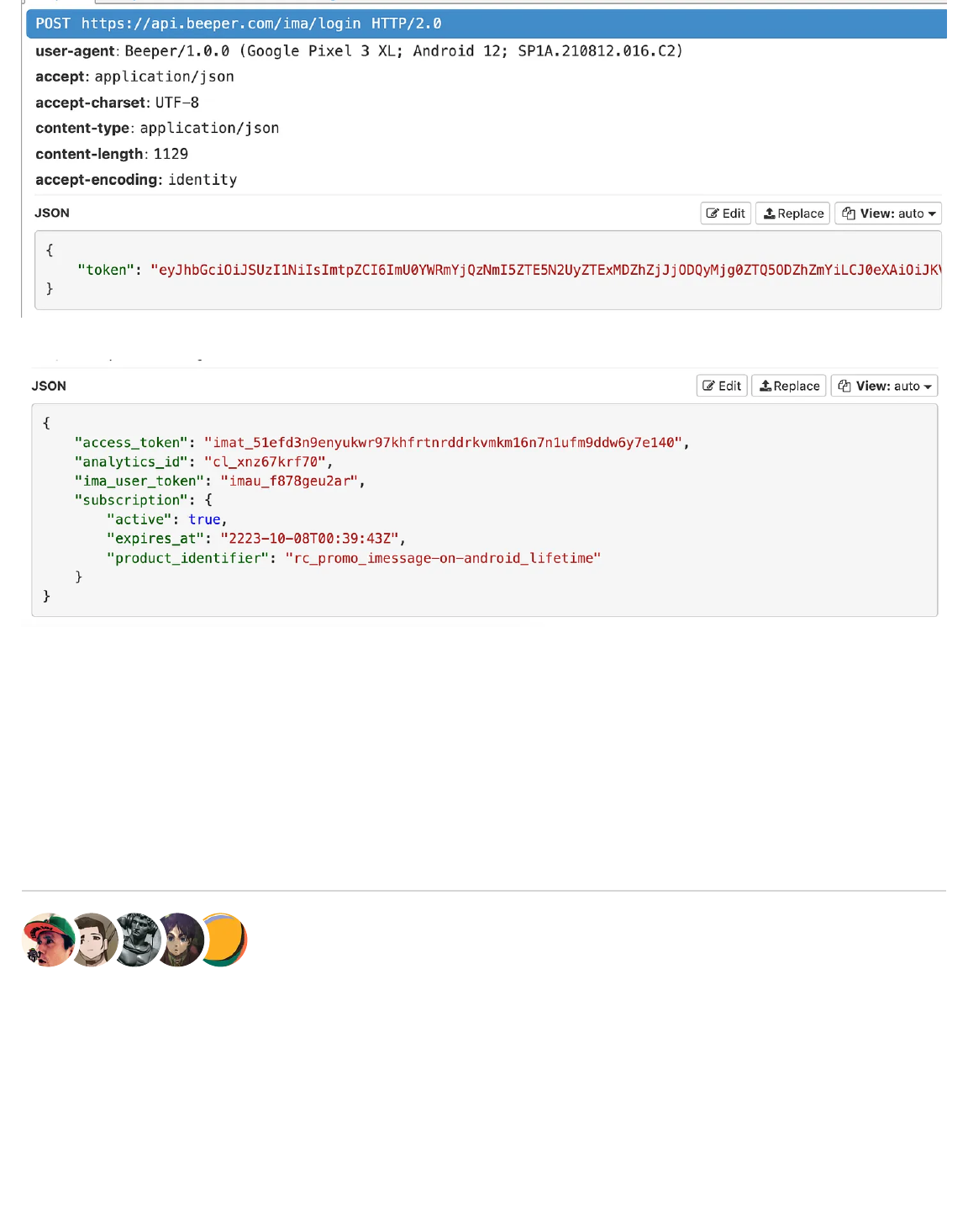
6"./&%(,%5%<51)3'"%/=%)+"%'"U3",),%)+5)%&"%?58"%&()+%:11."#,%,"'$"',%/$"'%`BBFK%&+"*
./00(*0%(*)/%(7",,50"%&()+%2/3'%1+/*"%*3?-"'9%!"%\',)%'"0(,)"'%&()+%5%,"'$(<"%*5?"4
albert.apple.com;%&+(<+%,"),%31%/3'%^13,+_%<'"4"*)(5.,%5*4%5../&,%3,%)/%</**"<)%)/
:FLK9%!"%)+"*%?58"%)&/%'"U3",),%)/%0")%)+"%*3?-"'%&"%*""4%)/%,"*4%5*%K7K%)/%'"0(,)"'
/3'%1+/*"%*3?-"'%&+(<+%(,%4(W"'"*)%=/'%"5<+%<5''("'%QB+(,%<51)3'"%&5,%)58"*%&()+%5%4"$(<"
'"0(,)"'"4%&()+%N/0"',;%5%X5*54(5*%<"..%1+/*"%<5''("'% R9%a(*5..2;%&"%)58"%)+"%</*)"*),%/=
)+"%'",1/*,"%K7K%Q*/)%,+/&*%+"'"R%5*4%,"*4%()%)/%identity.ess.apple.com;
'"0(,)"'(*0%/3'%5<</3*)%&()+%(7",,50"%5*4%0"*"'5)(*0%)+"%^(4"*)()2_%<'"4"*)(5.,%&"#..%3,"%)/
,"*4%5*4%'"<"($"9
Appendix

H1)(/*5..2;%2/3%<5*%5.,/%'"0(,)"'%2/3'%:11."%TP%&()+%6""1"'%7(*(%5,%&"..;%5,%,+/&*%(*%)+(,
<51)3'"9%M/3%\',)%1'/$(4"%2/3'%3,"'*5?"%5*4%15,,&/'4%/$"'%"*<'21)"4%`BBFK%4('"<).2%)/
:11."#,%,"'$"',;%=/../&"4%-2%5%,"</*4%'"U3",)%)/%1'/$(4"%2/3'%Ga:%</4"9%!"%<5*%)+"*
'"0(,)"'%=/'%(7",,50"%505(*;%)+(,%)(?"%1'/$(4(*0%)+"%<"')(\<5)",%='/?%-/)+%)+"%"5'.("'%1+/*"
*3?-"'%'"0(,)'5)(/*%5*4%/3'%*"&%:11."%TP%'"0(,)'5)(/*9%N"0(,)"'(*0%)+","%)/0")+"'%(*%)+"
,5?"%<5..%.(*8,%)+"?%)/0")+"';%5../&(*0%5*2%/)+"'%4"$(<"%)+5)%2/3#'"%./00"4%(*%&()+%2/3'
:11."%TP%)/%,"*4%5*4%'"<"($"%&()+%-/)+%2/3'%:11."%TP%"?5(.,%5*4%2/3'%1+/*"%*3?-"'9
L"E);%5%<51)3'"%/=%)+"%8"2,%,+5'"4%&()+%)+"%6""1"'%F3,+%L/)(\<5)(/*%,"$(<"%Q+/,)*5?"
imux.beeper.comR9%L/)";%)+"%NK:%1'($5)"%8"2%(*%)+(,%'"U3",)%(,%2/3'%^13,+_%<'"4"*)(5.,
)+5)%5../&%2/3%)/%</**"<)%)/%:FL,;%*/)%2/3'%^(4"*)()2_%<'"4"*)(5.,%)+5)%5../&%2/3%)/%"*<'21)
5*4%4"<'21)%(7",,,50",9%F3,+%<'"4"*)(5.,%<5**/)%-"%3,"4%)/%",<5.5)"%1"'?(,,(/*,%/'%5<<",,
5*2)+(*0%/)+"'%)+5*%)+"%1'","*<"%/=%5%*"&%:FL,%13,+%*/)(\<5)(/*9%X+"<8%/3)%apns.py%(*
1213,+%F/X%)/%."5'*%?/'"%5-/3)%13,+%<'"4"*)(5.,9

K"*4(*0%5*4%'"<"($(*0%(,%*/)%,+/&*%+"'";%5,%)+"2%5'"%*/)%4/*"%/$"'%`BBF%-3)%(*,)"54
)+'/30+%5*%KKO%"*<'21)"4%BXF%</**"<)(/*%)/%:FL,9%B+"%:FL,%,"'$"',%5'"%+/,)"4%5)%*-
courier.push.apple.com%;%&+"'"%)+"%5,)"'(,8%(,%'"1.5<"4%-2%5%*3?-"'%-")&""*%A%5*4
De9%:..%?",,50"%</*)"*),%5*4%?"4(5%5'"%"*<'21)"4%&()+%2/3'%^(4"*)()2_%8"2,;%&+(<+%*"$"'
."5$"%2/3'%:*4'/(4%1+/*"9
B+"'"%(,%5%/login%"*41/(*)%/*%6""1"'%,"'$"',;%-3)%5,%?"*)(/*"4%1'"$(/3,;%)+(,%(,%/*.2%=/'
,3-,<'(1)(/*%?5*50"?"*)%13'1/,",9%B+"%<.("*)%,3-?(),%)+"%)/8"*%'"<"($"4%='/?%)+"%[//0."
./0(*%1'/<",,%)/%/3'%,"'$"',;%5*4%)+"%'",1/*,"%</*)5(*,%)+"('%,3-,<'(1)(/*%,)5)3,9%L/
(7",,50"%<'"4"*)(5.,%5'"%"$"'%,"*)%)/%6""1"'%,"'$"',9

35
B. Apple uses APIs and other critical access points in the smartphone ecosystem
to control the behavior and innovation of third parties in order to insulate
itself from competition
i. Messaging: Apple protects its smartphone monopoly by degrading
and undermining cross-platform messaging apps and rival
smartphones
80. Apple undermines cross-platform messaging to reinforce “obstacle[s] to iPhone
families giving their kids Android phones.” Apple could have made a better cross-platform
messaging experience itself by creating iMessage for Android but concluded that doing so “will
hurt us more than help us.” Apple therefore continues to impede innovation in smartphone
messaging, even though doing so sacrifices the profits Apple would earn from increasing the
value of the iPhone to users, because it helps build and maintain its monopoly power.
81. Messaging apps allow smartphone users to communicate with friends, family, and
other contacts and are often the primary way users interact with their smartphones. In Apple’s
own words, messaging apps are “a central artery through which the full range of customer
experience flows.”
82. Smartphone messaging apps operate using “protocols,” which are the systems that
enable communication and determine the features available when users interact with each other
via messaging apps.
83. One important protocol used by messaging apps is SMS.
1
SMS offers a broad user
network, but limited functionality. For example, all mobile phones can receive SMS messages,
but SMS does not support modern messaging features, such as large files, edited messages, or
reactions like a “thumbs up” or a heart.
1
Following industry practice, throughout this complaint, “SMS” refers to both SMS and MMS (“multimedia
messaging service”). MMS is a companion protocol to SMS that allows for group messages and messages with basic
multimedia content, such as small file sharing.
Case 2:24-cv-04055 Document 1 Filed 03/21/24 Page 35 of 88 PageID: 35
36
84. Many messaging apps—such as WhatsApp, Facebook Messenger, and Signal—
use proprietary, internet-based protocols, which are sometimes referred to as OTT (“over the
top”) protocols. OTT messaging typically involves more secure and advanced features, such as
encryption, typing indicators, read receipts, the ability to share rich media, and disappearing or
ephemeral messages. While all mobile phones can send and receive SMS messages, OTT only
works between users who sign up for and communicate through the same messaging app. As a
result, a user cannot send an OTT message to a friend unless the friend also uses the same
messaging app.
85. Apple makes third-party messaging apps on the iPhone worse generally and
relative to Apple Messages, Apple’s own messaging app. By doing so, Apple is knowingly and
deliberately degrading quality, privacy, and security for its users. For example, Apple designates
the APIs needed to implement SMS as “private,” meaning third-party developers have no
technical means of accessing them and are prohibited from doing so under Apple’s contractual
agreements with developers. As a result, third-party messaging apps cannot combine the “text to
anyone” functionality of SMS with the advanced features of OTT messaging. Instead, if a user
wants to send somebody a message in a third-party messaging app, they must first confirm
whether the person they want to talk to has the same messaging app and, if not, convince that
person to download and use a new messaging app. By contrast, if an Apple Messages user wants
to send somebody a message, they just type their phone number into the “To:” field and send the
message because Apple Messages incorporates SMS and OTT messaging.
86. Apple prohibits third-party developers from incorporating other important
features into their messaging apps as well. For example, third-party messaging apps cannot
continue operating in the background when the app is closed, which impairs functionality like
Case 2:24-cv-04055 Document 1 Filed 03/21/24 Page 36 of 88 PageID: 36
37
message delivery confirmation. And when users receive video calls, third-party messaging apps
cannot access the iPhone camera to allow users to preview their appearance on video before
answering a call. Apple Messages incorporates these features.
87. If third-party messaging apps could incorporate these features, they would be
more valuable and attractive to users, and the iPhone would be more valuable to Apple in the
short term. For example, by incorporating SMS, users would avoid the hassle of convincing
someone to download a separate app before sending them a message. Third-party messaging
apps could also offer the ability to schedule SMS messages to be sent in the future, suggest
replies, and support robust multi-device use on smartphones, tablets, and computers—as they
have already done on Android.
88. Moreover, messaging apps benefit from significant network effects—as more
people use the app, there are more people to communicate with through the app, which makes
the app more valuable and in turn attracts even more users. Incorporating SMS would help third-
party messaging apps grow their network and attract more users. Instead, Apple limits the reach
of third-party messaging apps and reinforces network effects that benefit Apple.
89. Recently, Apple has stated that it plans to incorporate more advanced features for
cross-platform messaging in Apple Messages by adopting a 2019 version of the RCS protocol
(which combines aspects of SMS and OTT). Apple has not done so yet, and regardless it would
not cure Apple’s efforts to undermine third-party messaging apps because third-party messaging
apps will still be prohibited from incorporating RCS just as they are prohibited from
incorporating SMS. Moreover, the RCS standard will continue to improve over time, and if
Apple does not support later versions of RCS, cross-platform messaging using RCS could soon
be broken on iPhones anyway.
Case 2:24-cv-04055 Document 1 Filed 03/21/24 Page 37 of 88 PageID: 37
38
90. In addition to degrading the quality of third-party messaging apps, Apple
affirmatively undermines the quality of rival smartphones. For example, if an iPhone user
messages a non-iPhone user in Apple Messages—the default messaging app on an iPhone—then
the text appears to the iPhone user as a green bubble and incorporates limited functionality: the
conversation is not encrypted, videos are pixelated and grainy, and users cannot edit messages or
see typing indicators. This signals to users that rival smartphones are lower quality because the
experience of messaging friends and family who do not own iPhones is worse—even though
Apple, not the rival smartphone, is the cause of that degraded user experience. Many non-iPhone
users also experience social stigma, exclusion, and blame for “breaking” chats where other
participants own iPhones. This effect is particularly powerful for certain demographics, like
teenagers—where the iPhone’s share is 85 percent, according to one survey. This social pressure
reinforces switching costs and drives users to continue buying iPhones—solidifying Apple’s
smartphone dominance not because Apple has made its smartphone better, but because it has
made communicating with other smartphones worse.
91. Apple recognizes that its conduct harms users and makes it more difficult to
switch smartphones. For example, in 2013, Apple’s Senior Vice President of Software
Engineering explained that supporting cross-platform OTT messaging in Apple Messages
“would simply serve to remove [an] obstacle to iPhone families giving their kids Android
phones.” In March 2016, Apple’s Senior Vice President of Worldwide Marketing forwarded an
email to CEO Tim Cook making the same point: “moving iMessage to Android will hurt us more
than help us.”
Case 2:24-cv-04055 Document 1 Filed 03/21/24 Page 38 of 88 PageID: 38
39
92. In 2022, Apple’s CEO Tim Cook was asked whether Apple would fix iPhone-to-
Android messaging. “It’s tough,” the questioner implored Mr. Cook, “not to make it personal but
I can’t send my mom certain videos.” Mr. Cook’s response? “Buy your mom an iPhone.”
93. Recently, Apple blocked a third-party developer from fixing the broken cross-
platform messaging experience in Apple Messages and providing end-to-end encryption for
messages between Apple Messages and Android users. By rejecting solutions that would allow
for cross-platform encryption, Apple continues to make iPhone users’ less secure than they could
otherwise be.
Case 2:24-cv-04055 Document 1 Filed 03/21/24 Page 39 of 88 PageID: 39